Ubertooth Retirement
After 12 years and 17 production runs, Great Scott Gadgets is retiring our first product, Ubertooth One, from our hardware catalog.
GSG’s founder Michael Ossmann designed Ubertooth One because he wanted a device that could detect and monitor Bluetooth. At the time, such instruments existed but cost at least five figures—prohibitively expensive for most security researchers. His goal was to design an open-source, affordable-to-make tool that anyone in the security community with basic soldering skills could assemble. At the project’s inception, his intent was not to sell hardware but to provide a solution to a problem that no one else had solved. However, demand from the community prompted him to start GSG and launch a Kickstarter campaign that funded the first production.
Ubertooth One enabled more than starting a company; it became an essential part of the wireless security professional’s toolkit and aided research that improved Bluetooth security and function. One notable example is Mike Ryan’s Bluetooth Low Energy (BLE) security research. Through this work, Mike contributed BLE capabilities to Ubertooth and became a core developer of the project. More recently, Ubertooth One was instrumental in research into Apple’s Continuity protocol presented by Sam Teplov at ShmooCon in January 2020. Over the years, Ubertooth has equipped researchers to improve the Bluetooth protocol’s function and reverse engineer countless Bluetooth devices and even non-Bluetooth 2.4 GHz wireless systems such as electric skateboards. Talking to Michael this week about his journey with Ubertooth, I learned of an encounter at a conference in Asia where a stranger approached him and said “Thank you for Ubertooth. I couldn’t have done my Master’s thesis without it.”
At the time Ubertooth One was designed, BLE didn’t yet exist. The protocol now known as Bluetooth Classic was the only Bluetooth protocol. It was common for Bluetooth devices to operate in non-discoverable mode, making them invisible to all but the most expensive monitoring tools. Ubertooth One made it possible to detect and identify non-discoverable Bluetooth devices, an essential function for wireless security practitioners and researchers. Today, most Bluetooth devices use BLE rather than Bluetooth Classic, and several low-cost options are available for monitoring BLE. For more esoteric capabilities, including the detection of non-discoverable Bluetooth Classic devices, researchers can use Software Defined Radio platforms such as HackRF One to implement the same functions as Ubertooth. Even though Ubertooth is still a valuable and widely adopted tool, it is no longer the only option.
When the global chip shortage struck, our small team faced difficult choices about which products to redesign for available components. After considering changes in the Bluetooth landscape, the amount of redesign effort required, and the work cycles available to our team, we decided it was time to retire Ubertooth One. Consistent with our mission, we will continue to prioritize making and maintaining tools that, like Ubertooth in the early years, allow innovative people to do things they haven’t previously been able to do.
Even though we are now sold out of Ubertooth One, you may still be able to buy a unit made by GSG while reseller stock lasts. The Ubertooth project is open source, so if you can’t purchase an Ubertooth One, you are welcome to use the design files in the project repository to make your own. We will continue to monitor the repository for issues and pull requests, but we have no plans for hardware or software enhancements.
The Ubertooth project has meant a great deal to Great Scott Gadgets, and we’d like to sincerely thank our users, our resellers, and all the people who have supported us and contributed to the project over the years for coming on this journey with us. Special thanks to Dominic Spill, who started gr-bluetooth, which was foundational to Project Ubertooth; Jared Boone, who mentored Michael in the original hardware design; and Mike Ryan, who made significant contributions to the project. If you have any stories you’d like to share about Ubertooth One, please come tell them in the Great Scott Gadgets Discord server or email us at info@greatscottgadgets.com.
Shutting Down GSG Project-Specific Mailing Lists
Thank you to everyone who has been a part of the GSG project mailing lists. We at Great Scott Gadgets appreciate all of the conversations and friendships that have been forged on these lists. Over the last few years we have not given our project-specific mailing lists the attention they deserve; instead we have been focusing our efforts on Discord and GitHub. As such, we will be disabling all the mailing lists except for GSG-announce. Links to the mailing list archives for Ubertooth, YARD Stick One, GreatFET One, and HackRF will all remain available on their individual product pages. Current links to the archives are here:
Tools of the KNOB Attack
This week at USENIX three researchers published information about a new attack against classic Bluetooth. Known as KNOB, the attack takes advantage of a weakness in the Bluetooth specification to force target Bluetooth connections to use 8-bit encryption keys instead of larger keys that would be resilient against brute-force attack.
This weakness in classic Bluetooth (not Bluetooth Low Energy) is a big one. I don’t recall seeing such a significant vulnerability in Basic Rate Bluetooth security since pairing was improved with the introduction of Secure Simple Pairing in Core Specification v2.1 in 2007.
One of the things that intrigued me when I heard about the KNOB attack this week was that it sounded very familiar. After chatting with Dominic Spill, we’re pretty sure we discussed the potential for this attack about ten years ago. I’m fairly certain that I had highlighted Encryption Key Size Request in a printed copy of the specification around that time.
What we didn’t have back then was a way to test for this vulnerability. The specification allows for devices to reject key sizes they consider too small, and I guessed at the time that vendors would enforce a more reasonable minimum key size than the smallest (1 byte) allowed by the specification. As demonstrated this week by Daniele Antonioli, Nils Ole Tippenhauer, and Kasper B. Rasmussen, I was wrong!
In order to test this attack it is necessary to modify the behavior of the Link Manager, the part of a Bluetooth chip that creates logical links with other Bluetooth devices. The Link Manager Protocol (LMP) is the low layer protocol that Link Managers use to communicate with one another and negotiate things including encryption for protection of higher layer protocols. LMP messages are not visible over the Host Controller Interface (HCI) that carries information between a Bluetooth chip and an application processor. If you only have the ability to control a Bluetooth chip by modifying an Operating System driver, you can alter behavior at the HCI level but not the LMP level. Ten years ago I was working on creating tools for monitoring Bluetooth signals, and I used off-the-shelf Bluetooth adapters for security testing, but I didn’t have any tools capable of active attacks below the HCI layer.
Last year things changed when Dennis Mantz released InternalBlue along with his award winning master’s thesis. Dennis reverse engineered the firmware of a popular Bluetooth chip and with InternalBlue provided a method to alter the firmware, enabling modification of Link Manager behavior for the first time. Since then Dennis and Jiska Classen have published a series of papers and presentations demonstrating powerful uses of this important tool.
It was InternalBlue that enabled the KNOB researchers to test attacks against key size negotiation for the first time. They used InternalBlue to implement a man-in-the-middle attack that inserted requests for a key size of one byte and successfully demonstrated the attack against nearly every Bluetooth device they tested. This weakness existed in the Bluetooth specification for twelve years, but nobody had tools to test it. Once a tool became available, KNOB was discovered within a year.
Another tool used by the KNOB researchers was Ubertooth One, the open source Bluetooth monitoring platform I designed almost a decade ago. They used Ubertooth One to eavesdrop on encrypted packets in order to prove the weakness of the encryption after forcing a key size of one byte. They correctly point out in their paper that Ubertooth One lacks an effective ability to follow the hopping sequence of classic Bluetooth connections (it is better at this with Bluetooth Low Energy, thanks to Mike Ryan), but they worked around that problem by capturing a single packet and then iterating over all possible clock values to interpret the packet. This ingenuity allowed them to use the low cost Ubertooth One instead of a Bluetooth analyzer costing tens of thousands of dollars.
The KNOB researchers demonstrated that Wright’s Law still holds true after all these years:
“Security will not get better until tools for practical exploration of the attack surface are made available.” –Josh Wright
Discovering the Bluetooth UAP
During an interview the other day I was asked to describe how we determine the UAP of a Bluetooth address with Ubertooth. A few minutes after the interview I realized that I oversimplified and got one detail wrong: I mentioned whitening when I should have talked about the HEC and CRC. Considering that only a few people in the world have intimate knowledge of our method, I thought it would be a good idea to describe it more thoroughly and correctly for posterity. It’s complicated, and I don’t think we’ve ever attempted to fully describe it anywhere but in the convoluted source code of libbtbb.
I’m writing about classic Bluetooth, by the way, not Bluetooth Low Energy (LE) also known as Bluetooth Smart. In general, these sorts of things are easier with LE, so they do not require such long-winded explanations.
The Upper Address Part (UAP) is a particular 8 bit section of a Bluetooth Device Address (BD_ADDR). In order to fully decode Bluetooth packets, determine a Bluetooth hopping sequence, or do anything else interesting with Bluetooth, we need to know the UAP in addition to the Lower Address Part (LAP) of the piconet’s master device.
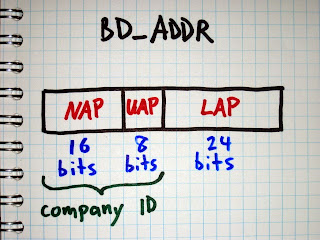
The master’s 24 bit LAP is easy to discover using a tool like Ubertooth that can demodulate Bluetooth packets. Every Bluetooth packet includes the master’s LAP as a part of the sync word at the beginning of the packet. It is transmitted in the clear, so we only have to capture and demodulate one packet in order to learn the LAP.
The UAP is harder to determine, but there are multiple methods available to us. The simplest method is brute force search. As Joshua Wright showed in Hacking Exposed Wireless, Second Edition, it is possible to try connecting to a target’s BD_ADDR over and over, guessing a new UAP each time. Because the Non-significant Address Part (NAP) is ignored during the initial connection process, it doesn’t matter what value we use; we only need the correct LAP and UAP. Since the UAP is 8 bits, there are only 256 possible values to try, and a correct match can typically be found quite quickly by prioritizing common UAPs, possible because the UAP is part of the Organizationally Unique Identifier (OUI) assigned to manufacturers (and there is a fairly small number of companies that make the majority of Bluetooth devices). Common UOIs can be identified thanks to the BNAP BNAP project.
Brute force is an excellent method to have in our toolbox, but it has some drawbacks. First, it is an active attack that can influence the behavior of the target devices and that can be detected by a monitoring system. Second, it only works if the master device is in a connectable state. Many devices do not enter the connectable state when they already have an active connection. Annoyingly, many devices are connectable for only brief periods of time (one out of every five seconds, for example), slowing down a brute force search.
The Ubertooth project aims to provide the best possible tools for passive monitoring of Bluetooth systems, so we implement a method of UAP discovery that does not require active transmission.
We think of the problem as being a search for the correct UAP out of a search space that is 8 bits in size (having 256 candidates). We do not have any method to observe the UAP directly, so we instead perform a series of techniques that reduce the search space by a process of elimination until only one possible UAP remains.
Our first technique is to compute the UAP by reversing the Header Error Check (HEC) that appears at the end of the header of every packet that has a header. The HEC is an 8 bit value computed from the master’s UAP and the header bytes. The purpose of the HEC is to allow a receiver to verify that the packet header was received correctly, without any unrecovered bit errors. We assume that we received the packet without bit errors (which is true most of the time). After decoding the HEC and the packet bytes it is possible to determine the one missing variable, the UAP. This is particularly easy because Bluetooth’s HEC algorithm is reversible; we can run it forward to determine the HEC from the UAP and packet bytes, or we can run it backward to determine the UAP from the HEC and packet bytes.
Apart from the ID packet type which is transmitted frequently during inquiry (searching for devices) and paging (connecting), every Bluetooth packet contains a header with HEC. This makes it possible for us to perform this technique frequently for a busy piconet even though we are monitoring only one out of 79 channels.
This may sound like an easy victory, but it is complicated by one significant problem: whitening. Every Bluetooth packet is whitened or scrambled by XOR with a pseudo-random bit sequence before transmission. Since the packet header is whitened, we have to unwhiten it before we can reverse the HEC algorithm.
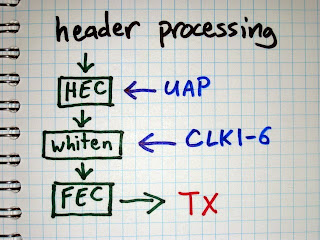
There are 64 possible pseudo-random sequences that can be used to whiten a packet. The particular sequence is selected by the lower six bits of the master’s clock (CLK1-6) that is used for other things such as synchronizing the frequency hopping pattern.
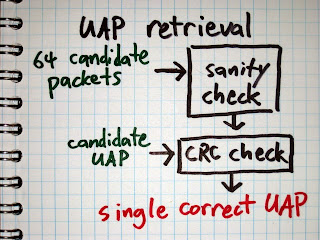
When we receive a packet, we try each of the 64 possible CLK1-6 values. For each value, we determine the whitening sequence, unwhiten the packet using that sequence, and reverse the HEC algorithm to determine the UAP. This gives us 64 candidate UAP values, so we’ve reduced the search space from 8 bits to 6 bits. Because we have a way to compute the UAP for a particular CLK1-6, we take the approach of trying to determine CLK1-6.
There is one easy way to determine the correct CLK1-6. If a packet has a payload that includes a Cyclic Redundancy Check (CRC), then we can use the CRC to verify that we have unwhitened the packet correctly. If one of our 64 possible CLK1-6 values results in a CRC match, then we win.
Up to this point, this method was described in BlueSniff: Eve meets Alice and Bluetooth.
The main problem with the CRC method is that it only works on packets that have CRCs. If you look through the Bluetooth Core Specification, you’ll find that only certain packet types have payloads with CRCs, and it turns out that these are the minority of Bluetooth packets in the wild. It is very common to see thousands of packets from a piconet without ever capturing one CRC with Ubertooth. Because of this, we needed another method to determine if a CLK1-6 value is correct or incorrect.
The next method we use to validate CLK1-6 is to perform a series of sanity checks on the packet format. The unwhitened packet header includes a four bit packet type field. If, for example, the packet type field is 5, then we know that it is an HV1 packet. HV1 packets do not have CRCs, but they have a payload encoded with a 1/3 rate Forward Error Correction (FEC) method implemented by repeating every bit three times in a row. Since different packet types use different FEC methods, we can perform a sanity check that verifies that every bit is repeated three times for the expected packet length (with some allowance for bit errors). If the FEC check fails, then we can be pretty sure we have the wrong CLK1-6 value.
Up to this point, this method was described in Building an All-Channel Bluetooth Monitor.
Unfortunately, CRC and sanity checks are not as useful as you might think. Originally we thought that we could simply look for correct CRCs, but they turned out to be rare. Then we thought that we could use a process of elimination where incorrect CRCs or sanity check failures would allow us to remove large numbers of candidate CLK1-6 values, but those cases also turned out to be less frequent than we thought.
The main reason we are often unable to eliminate a candidate CLK1-6 value is that Bluetooth has more than sixteen packet types, so the 4 bit packet type field in the header is overloaded. Here’s an example:
For a trial CLK1-6 value, the packet type field is decoded as 10. This could indicate that the packet type is DM3, a data packet carrying 2 to 123 data bytes and a CRC, or it could indicate that the packet type is 2-DH3, an Enhanced Data Rate (EDR) packet that uses a modulation for the payload that cannot be demodulated by Ubertooth One. (We can demodulate the packet header but not the payload.)
Without prior knowledge of the state of the piconet, we don’t know which of the two packet types is present. We assume it is a DM3 packet and check for a CRC. If we get a CRC match then we win, but this is rare. More often the CRC check fails. This means one of two things: Either the CLK1-6 value is wrong, or the packet is actually a 2-DH3 packet that we can’t verify. Since we can’t verify one of the possible reasons for CRC failure, we can’t eliminate that CLK1-6 value from our list of candidates.
Some of our CRC and sanity checks have a positive result indicating a correct CLK1-6. Some of them have a negative result indicating that the CLK1-6 value can be eliminated. However, the majority of our checks have an inconclusive result. This means that the process of elimination is rarely successful with just one packet.
Fortunately Bluetooth piconets tend to transmit packets fairly often, so we can continue the process of elimination across multiple received packets. Once we have the first packet, we can usually reduce the 64 CLK1-6 values to 50 to 60 candidates. With each subsequent packet, we can usually eliminate a few more candidates, but it is tricky.
The trickiness has to do with inter-packet timing. All packets are transmitted in time slots dictated by the master’s clock. We know how often the clock increments, and we have guesses as to the lower 6 bits of the clock. When we receive a subsequent packet, we can measure the time interval from one packet to the next and determine how many time slots have elapsed. This tells us how much to increment our original guesses when testing the new packet.
This would be a fairly reliable method if it were possible to have two clocks perfectly agree with each other. The crystal on Ubertooth One meets the requirements of the Bluetooth specification, so it is just as good as any Bluetooth device (with a frequency stability of 20 ppm). However, we don’t know how much faster or slower the target master’s clock is compared with the clock on the Ubertooth. It might be as much as 40 ppm different. Even if we had the best clock in the universe on Ubertooth, the target master’s clock will still drift by up to 20 ppm (assuming it is operating within spec).
Because of clock drift, we sometimes eliminate a candidate CLK1-6 value that might be correct simply because we counted the wrong number of time slots between packets. Additionally, bit errors in packets may cause us to incorrectly eliminate a candidate (e.g. if the bit error caused a CRC failure on a packet type without an overloaded packet type field). These things happen, and that’s why UAP discovery sometimes fails with zero candidates remaining. In these cases we simply start the process over as new packets arrive, and we usually get a correct result before having to restart very many times.
A nice enhancement to the code would be consideration of the maximum possible clock drift when computing time slot intervals. If we considered three intervals instead of one, for example, we might avoid a lot of cases where we improperly eliminate the correct CLK1-6 value. Additionally, we could benefit from keeping a running estimate of the master’s clock drift after we have determined the UAP.
A problem people sometimes have with Ubertooth is that the correct UAP is determined but is subsequently lost. This happens because a packet is received that doesn’t agree with the previously determined UAP, probably because of bit errors but possibly due to clock drift. Since we have an all-or-nothing approach to determining the UAP, a single disagreement can result in losing the correct value. Another nice enhancement would be maintaining a confidence value for the current UAP (or perhaps for multiple candidates). If a UAP has proven correct for 1000 packets, it would be nice not to throw it out when one packet disagrees. This would complicate some already convoluted code, but it is definitely worth trying.
Overall, we have a very effective method of determining the master’s UAP through passive monitoring. It is complicated, but it is only a small part of the even more complicated process of determining a piconet’s frequency hopping pattern and hopping along.
Ubertooth Release 2014-02-R2
After a very long break, we are pleased to announce a new release of Ubertooth and libbtbb code. Release notes are given below but for those short on time, the summary is: a major update with complete rewrites of the libbtbb API, greatly improved BTLE support and a migration to GitHub. You can find the release here.
Release Notes
The Ubertooth host utilities in this release require libbtbb-2014-02-R2 or greater.
The release archive is ubertooth-2014-02-R2.tar.xz, it contains binary firmware images and PCB layouts as well as the project source code. The source code links do not include the binary files.
These are just the highlights, for a complete list of changes since the previous release, see the git commit log.
-
Bluetooth Smart (Low Energy) Support
- Promiscuous and follow modes
- Pcap format packet logging
- Pairing / encryption support when paired with crackle
- Credit for BLE features goes to Mike Ryan
-
Unified host tool for monitoring Basic Rate
- ubertooth-rx replaces -lap, -uap, -hop tools
- Once UAP is discovered, ubertooth-rx automatically tries to find clock values and begin hopping
- Thanks to Will Code for working on this
-
Survey tool - ubertooth-scan
- Combining both Ubertooth and a standard Bluetooth dongle
- Ubertooth scans for non-discoverable master devices
- Dongle probes devices for piconet information and features
-
Cmake now used for the build system
- Improves support for non-Linux operating systems
- More sensible handling of dependencies
- New build instructions
-
Packaging (Experimental)
- Early stage support for packaging systems
- libbtbb in Homebrew repository, Ubertooth coming soon
- MacPorts availability is under test
- Release already available in Pentoo
-
GitHub migration
- libbtbb, Ubertooth and gr-bluetooth all hosted on GitHub
- Allows for more open development and collaboration model
- Already seeing an increase in issue reporting and pull requests
Speeding up CRC calculations for Bluetooth Low Energy
Over the past few days Mike Ryan has been working hard to cram as much of the Bluetooth Low Energy (BTLE) functionality as possible in to the Ubertooth firmware. In doing so he plans to relieve the host system of the work involved in finding and processing packets. In time this will allow Ubertooth to monitor and inject packets in to BTLE connections while running from a very low powered host, or possibly without a host system at all.
This has involved some excellent work using the CC2400 chip to automatically detect BTLE packets, a task which it is unfortunately unable to achieve for basic rate Bluetooth. Once we know where a packet starts we are able to handle the packet data as a set of bytes rather than needing to break the data up in to bits before running through the whitening and CRC algorithms.
While Mike worked on the whitening algorithm, he set the CRC as an open challenge, which I gladly took up. I thought that it may make an interesting post to explain how CRC algorithms are implemented and show how to trade off time for memory, or time for space complexity for the computational theorists among us, by using a look up table (LUT). This may be common knowledge to many people and there are automated tools to achieve it, but I wanted to work it out by hand.
This part is, at least in part, for my own reference when I look at the code in a year’s time and ask “who did that? And how o we know it’s correct?”
Linear Feedback Shift Registers
Linear Feedback Sift Registers (LFSRs) are often used for CRC checks, forward error correction or to generate pseudo-random data. They are computationally cheap and simple to implement in hardware if required, so they are perfect for low cost networking chips. Bluetooth uses them to implement data whitening, header error checks, CRCs and forward error correction on packet data.
The LFSR that implements the CRC on BTLE packets looks something like this:
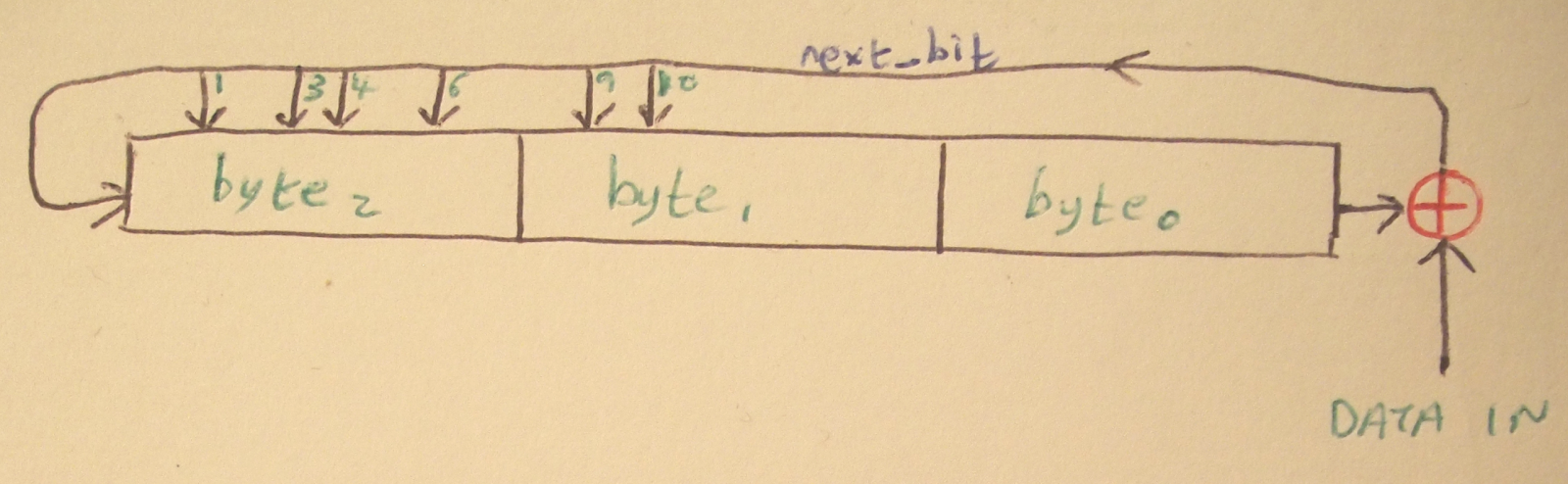
The LFSR for CRC on BTLE packets as drawn by me. See Vol 6, part B, Section 3.2 of the Bluetooth specification for a better, but non-free version of the diagram. For simplicity we can imagine the LFSR as parts, a shift register and the feedback element, using XOR. Each incoming bit of packet data is XOR’d with the right-most bit of the register, for consistency we’ll assume that the bits are numbered 0-23 from left to right. Bit 23 is XOR’d with the incoming data bit and becomes next_bit. The register is shifted one bit to the right and next_bit is added to the end, becoming bit 0. This is a shift register.
Now for the feedback part, each of those arrows feeding in to the top of the register represents a bit in the register that will be XOR’d with next_bit. T\hat is all you need to know about LFSRs for most usese, in fact it should be trivial to implement one using the above information. Here’s our implementation of the above LFSR:
u32 btle_calc_crc(u32 crc_init, u8 *data, int len) {
u32 state = crc_init;
u32 lfsr_mask = 0x5a6000; // 010110100110000000000000
int i, j;
for (i = 0; i < len; ++i) {
u8 cur = data[i];
for (j = 0; j < 8; ++j) {
int next_bit = (state ^ cur) & 1;
cur >>= 1;
state >>= 1;
if (next_bit) {
state |= 1 << 23;
state ^= lfsr_mask;
}
}
}
return state;
}
Optimising the LFSR
As you can see, we run through the inner loop for each bit of data, although we only perform the XOR if we next_bit was set. This is a very small optimisation that makes use of the shift operation filling with 0s and the fact that XOR with 0 would have no effect. Logically this process looks a little like this:

The LFSR split in to a shift and a feedback, or XOR, component. The diagram above shows the two stage LFSR, with the second stage containing the different masks to be XOR’d with the register depending on the state of next_bit. This is a two value look up table holding 24 bits od XOR mask.
If we can shift then look up the XOR for one bit, why not more? As long as we shift by the appropriate amount, the XOR result only relies on the incoming data and the state of the register. Even better, there is no feedback in to the lowest byte of the register, so early bits in an incoming byte don’t affect the value of later bits.
Working with Bytes
Taking a byte of input data, we first XOR it with the lowest byte of the register to get next_byte, then we shift the register to the right by a byte and append next_byte. This takes care of the shift.
To finish off we need to apply the eight XOR masks based on the content of next_byte. As the register is shifted for each bit, the masks are XOR’d together with each successive mask shifted by one bit, this is shown in the diagram below.

The final mask is produced by XORing the mask for each bit of next_byte.
The derived mask is specific to the next_byte value of 01101101, so we are able to store it in a table and retrieve it for future use. If we do this for all 256 values of next_byte we can build a full look up table, and use it to calculate the CRC.
The following code implements the CRC using a LUT:
u32 crcgen_lut(u32 crc_init, char *payload, int len)
{
u32 state = crc_init;
int i;
u8 key;
for (i = 0; i < len; ++i) {
key = payload[i] ^ (state & 0xff);
state = (state >> 8) ^ crc_lut[key];
}
return state;
}
The LUT itself consists of 256 32bit values, so is too large to reproduce here, but it can be found on Github.
While it is possible to write code to that builds the LUT from shifted masks for each value of next_byte, it was easier to use the known good implementation of the CRC algorithm given earlier to provide the final state of the register for all one byte payloads and then XOR it with the pre-mask state, as shown below.
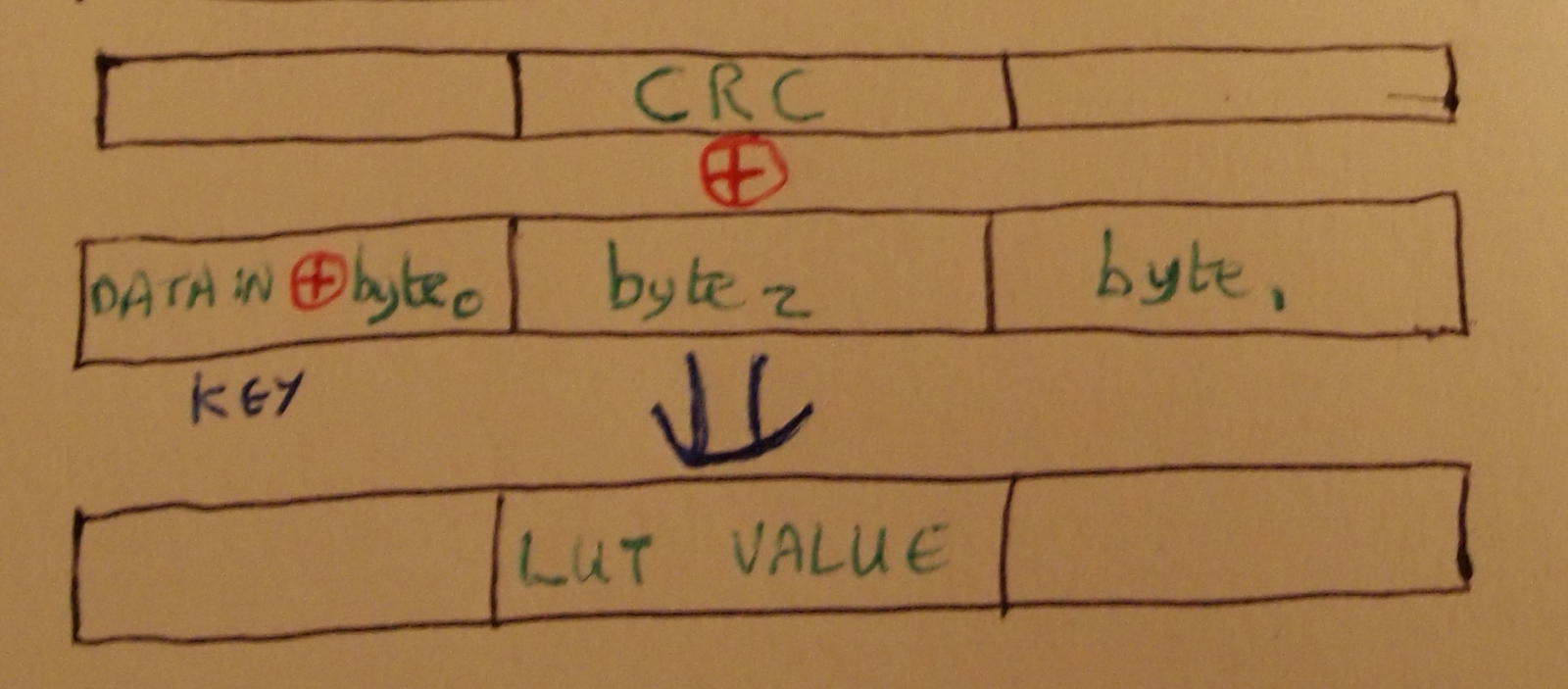
The XOR mask for each key is calculated and then stored in the LUT. After looking at the code, Michael Ossmann pointed out that leaving the key byte blank while building the LUT would yield the same result and avoid a pointless shift operation in the final algorithm. It seems that no matter how nerdy you try to be, someone will out-geek you.
Motivating the Problem
One of the most difficult aspects of talking to people about Bluetooth packet sniffing is what my university supervisor called “motivating the problem”. What he meant by this was trying to convince others that the problem which you were trying to solve was really as hard as you know it to be.

Over the past five years we have dedicated a lot of time to motivating the problem when we give presentations on Bluetooth security, often resulting in glazed looks from some audience members. This post is intended to go some way towards explaining the challenges facing our project and to encourage anyone interested to participate.
Bluetooth packet sniffing falls foul of the motivation problem because it is so often compared to other wireless protocols that appeared at around the same time, such as 802.11 and Zigbee, which had promiscuous packet sniffing solutions available, using commodity hardware, soon after their release.
Another reason that Bluetooth sniffing is hard to discuss is the set of terms that need to be defined before we can even begin to describe the problems involved. At a minimum, the following are useful to know before entering in to a discussion about Bluetooth packets:
Piconet - A personal area network with one master device connected to potentially many slave devices.
Master device - The device that defines a piconet, often but not always the “smartest” device, e.g. a PC or phone.
Slave device - The device being connected to the master, e.g. a keyboard, mouse or headset.
Bluetooth Device Address - A 48 bit unique device address, usually shown in the same format as IEEE 802 MAC addresses and issued from the same address space. It is common for smartphones to have consecutive Bluetooth device and wifi MAC addresses.
NAP - Non-significant Address Part. The first two bytes of the device address.
UAP - Upper Address Part. The third byte of the device address. Forms the organizationally unique identifier when combined with the NAP.
LAP - Lower Address Part. The lower three bytes of the device address, assigned by the manufacturer.
CLK27 - A 27 bit counter that increments 3200 times per second and wraps in slightly less than 24 hours. Every device maintains an internal clock value, although we are mostly concerned with the master device’s clock. Often referred to as “the clock”.
CLKN - The upper 26 bits of CLK27. This is a clock that ticks 1600 times per second, once per packet “slot”.
AFH Map - Adaptive Frequency Hopping allows Bluetooth connections to avoid using noisy channels, such as channels that overlap nearby wireless networks. The map specifies which channels are available for a given connection.
The feature of Bluetooth that makes packet sniffing so hard is frequency hopping. Originally designed to ensure robust connections, it causes more problems and confusion for packet sniffers than any other feature. The pseudo-random hopping sequence that all devices within a piconet share is determined by the LAP, UAP and CLKN of the master device. To have any chance of extracting useful data from a Bluetooth connection we need to know these three values.
The situation gets even worse for encrypted links. To have any chance of sniffing the pairing process, and using the extracted data to find the pin (see: http://www.eng.tau.ac.il/~yash/shaked-wool-mobisys05/index.html ), we must know these three values before the target devices begin to communicate.
One solution to this is to begin sniffing all traffic in a target piconet on the assumption that a new device will be paired with it in the future. In many ways it is good that this is not a practical attack vector, however it makes research and investigation in to Bluetooth authentication and encryption a harder task.
Devices that support Bluetooth v2.0+ also support adaptive frequency hopping (AFH), which adds an additional variable to the list that we have to find before we can monitor a connection.
The Ubertooth tools passively monitor each channel in turn to find piconets and build up information on the LAP, UAP, CLKN and AFH map, this behaviour can be seen in the Kismet plugin. Ubertooth-follow is the one exception to this method as it uses a Bluetooth dongle to acquire the values that the Ubertooth needs to follow a hopping pattern.
Hopefully this has provided a crash course in Bluetooth packet sniffing for anyone who wants to get involved or try out the Ubertooth tools. We’re working hard to improve the amount of data that we are able to collect as well as adding features such as packet injection, Bluetooth Low Energy support, integration with external tools such as Wireshark and Kismet and support for more low cost embedded platforms such as ARM (raspberryPi, BeagleBone) and Android.
So You Want to Track People with Ubertooth
I am contacted frequently by people who want to use Ubertooth One to track the movements of vehicles or pedestrians on highways, at airports, in shopping malls, etc. This is a FAQ.
Q: Can Ubertooth One be used to monitor movements of people carrying Bluetooth devices?
A: Yes. With multiple Ubertooth Ones covering different locations, you can determine the time that a particular target device is present at each location. This could allow you to compute average travel times on highways, wait times in queues, etc.
Q: We currently track Bluetooth devices by using standard Bluetooth adapters performing frequent inquiries. This only detects discoverable devices. Ubertooth One could be used to track non-discoverable devices, right?
A: Yes. However, Ubertooth One only detects devices when they are actively transmitting. An idle target device, discoverable or not, will not be detected by Ubertooth One in passive monitoring mode. Inquiry detects discoverable devices whether or not they were active before inquiry; passive monitoring detects active devices whether or not they are discoverable.
Q: So an optimal solution to identify the largest number of devices would incorporate both inquiry and passive monitoring?
A: To identify the most devices possible, you should use both inquiry and passive monitoring. Additionally you could perform paging or partial paging. Paging is the process used when a Bluetooth device connects to another. Once you have identified a non-discoverable Bluetooth device address with passive monitoring, you can page for that address. This determines whether or not the target device is present even if the device has become inactive.
Q: How is partial paging different than normal paging?
A: The normal paging procedure involves several packets transmitted back and forth between the master (the paging device) and the slave (the paged device). The first packet is transmitted by the master and contains the slave’s address. The second packet is transmitted by the slave in response to the master. It is possible for the master to stop the paging procedure at this point before fully opening the connection. The first slave response packet is sufficient to determine the slave’s presence. (This is analogous to a TCP SYN scan.) This partial paging procedure would be faster than a complete paging procedure. I don’t know of any implementations, but Ubertooth One would be a good platform for developing such a thing.
Q: Could partial paging be used to conduct a brute force search for all possible LAPs (Bluetooth Device Address Lower Address Parts)?
A: Yes, but it would take a while. Even with some optimizations, I estimate that an exhaustive brute force LAP search by partial paging with a single Ubertooth One would take on the order of 100 hours. This is considerably faster than previous implementations but is probably too slow to be useful for tracking applications.
Q: Could packets transmitted by paging or partial paging be misinterpreted by a nearby passive monitor, indicating presence of a device that is not there?
A: Yes. If you implement both paging and passive monitoring, you must take care to ignore the packets transmitted by your own system.
Q: We’re tracking Bluetooth devices anonymously.
A: No, you’re not.
Q: No, really! We are! Aren’t we?
A: Unless your system has been designed carefully for anonymity and has been audited thoroughly for anonymity by an information security professional, it is highly unlikely that you are tracking people anonymously. If you store BD_ADDRs (Bluetooth Device Addresses) of target devices, you are storing individually identifiable information about the owners of those devices. The same is true if you store hashes of BD_ADDRs or encrypted BD_ADDRs unless great care has been taken to irrevocably destroy encryption keys. If you delete stored data without an audited secure erasure procedure, you should assume the data are easily recoverable. Most importantly, if you tell people that their information is being anonymized without properly anonymizing it, you are a bad person.
Q: Are you interested in building a tracking system for us?
A: I am interested, from an academic standpoint, in tracking the movements of Bluetooth devices, and I believe that people have a right to know how they can be tracked by transmissions from wireless communication devices they carry. I would be willing to develop special purpose hardware and software for such applications so long as I am permitted to publish everything I produce under an open source license.
Q: We would like to pay you to develop a proprietary tracking system and grant us exclusive distribution. Will you do it?
A: I develop only open source hardware and software.
Discovering Bluetooth Devices
In July 2011 Michael Ossmann wrote a blog post entitled “Discoverability is Not a Mitigating Factor” which discussed the Bluetooth security advice being given about discoverable devices by people and organisations that should know better. It is worth reading his post in full, but I’ll quote two important parts here:
“LAP sniffing is easy. Spill and Bittau showed how to sniff LAPs with a USRP for about $1000. Now it can be done with an Ubertooth One for about a tenth of that price. It can even be done using Travis Goodspeed’s method for promiscuous sniffing with lower cost platforms.”
“The UAP is only slightly more difficult for an attacker to learn. Project Ubertooth and gr-bluetooth include software that implements automatic UAP determination based on passive observation of just a few packets.”
I completely agree with Michael on this, the methods for retrieving the LAP and UAP are easy and well known, but we still hear advice suggesting that turning off the discoverable setting for your device will protect it from being found by malicious attackers. So, taking in to account Wright’s law:
“Security will not get better until tools for practical exploration of the attack surface are made available.” -Josh Wright
I wrote a tool that would initiate a standard Bluetooth device scan, but also add devices discovered with the Ubertooth. I call the tool “ubertooth-scan” and it’s available from the master branch of the Ubertooth git repository.
Ubertooth-scan requires an Ubertooth and a standard Bluetooth device on a host with libbluetooth (bluez) installed. First we use the Bluetooth device to perform an HCI scan, this is the same as running “hcitool scan” from the command line. The second part of the tool uses the Ubertooth to promiscuously sniff for Bluetooth packets, retrieving the LAP and UAP values before handing them over to libbluetooth to query the device name. Most non-discoverable devices respond to name inquiries.
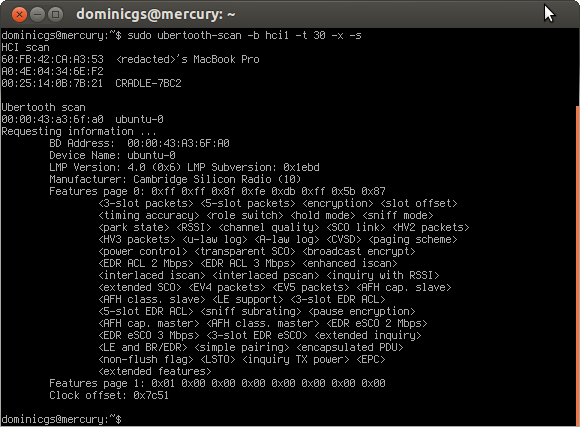
I’ve also added an extended query (triggered by the -x option) which will check the device for supported features, chipset version and clock offset from the local device.
Using a dongle to get the clock offset for a remote device allows us to calculate the clock value of the target and use that to hop along with the piconet, dumping packet data to screen as we go. Here’s a quick snippet of the code in action, apologies for the low quality video:
Note from 2022: The video that was in this post is no longer available.
I’ll be presenting this in more detail, along with other recent developments in the Ubertooth project, at Ruxcon this weekend. If you are in Melbourne or are already planning to attend Ruxcon, and would like more detail, please come to my presentation at 2pm on Sunday in track 1.
Ubertooth and libbtbb Release 2012-10-R1
The latest release of the Ubertooth software is now available. The 2012-10-R1 release contains numerous bug fixes and minor improvements as well as some large architectural changes.
The host code for both Ubertooth and libbtbb is now easier to compile, with major simplifications to the process for the btbb Wireshark plugin. Build instructions can be found on the Ubertooth website.
As development has shifted from a subversion repository to a git repository, we no longer have sequential revision numbers to use for release naming. All future releases will be named using the year and month of release.
When using the latest release it is necessary to update the firmware on your Ubertooth. Binary firmware images can be found in the release package, and flashed to the Ubertooth using the ubertooth-dfu tool (ubertooth-dfu –write <image-filename.dfu> –detach). The host code needs to be built and installed before updating firmware images. Alternatively firmware images can be built using the ARM embedded variant of gcc.
The release notes for the ubertooth 2012-10-R1 release are as follows:
Release Notes
The Ubertooth host utilities in this release require libbtbb-2012-10-R1 or greater, it can be found at https://sourceforge.net/projects/libbtbb/files/.
These are just the highlights. For a complete list of changes since the previous release, see the git log.
- libubertooth
The core Ubertooth functions are now packaged as a library, which allows us to have some independence between the core ubertooth functions and the tools that use them, such as ubertooth-* and the kismet plugin. This should also help with future binary packaging.
- Firmware flashing
The ubertooth-dfu tool now attenpts to identify Ubertooth devices and put them in to firmware upgrade mode. Multiple arguments can also be passed to ubertooth-dfu and will be executed in the order specified ont he commandline. To flash firmware on to an ubertooth device, use the following command: ubertooth-dfu –write <firmware_image.dfu> –detach
- Bluetooth Low Energy (Experimental)
Bluetooth Low Energy (Bluetooth Smart) sniffing is experimentally supported by the bertooth-btle tool. The tool can be used to sniff the connection setup procedure between devices; promiscuous sniffing is available but is extremely experimental. Credit for this achievement goes to Mike Ryan.
- Ubertooth-follow
Ubertooth-follow has been added to the set of Ubertooth commandline tools. It retrieves the clock value from a local device using libbluetooth (bluez) and uses the Ubertooth to hop in time with the piconet. To build ubertooth-follow use “make clock_debug=true”.
- Git
Since the last release we have moved the source repository from SVN to Git. This should not affect the released code, but makes life easier for those of us working on the code.
